Once you have figured out how to invest in cryptocurrencies, the next step is to pick out one or a combination of cryptocurrency wallets to store your keys.
With different types of cryptocurrency wallets, opinions on what the best option is keeps varying from person to person.
We list the various types of cryptocurrency wallets along with their pros and cons to help you make an informed decision.
Before we get into it, you need to understand the concept of Public and Private Keys. This is because wallets essentially work on storing these keys rather than storing coins (wallets DO NOT store coins).
Public & Private Keys
Rule of Thumb : Cryptocurrencies are not exactly “owned” by someone who purchases them in the traditional sense of ownership. Rather, think of it as more like assuming control of a certain amount of coins that exist in the blockchain network. You can manage it, move it around, make purchases with it, or convert it into fiat money.
Private Keys – They are the gateway to unlocking your access to perform any of the actions mentioned above. Without a private key, it is impossible to access your assets within the blockchain network. Hence you have to ensure security of your keys. This is because anyone with access to your private keys gets access to your coins associated with those keys.
Private keys act like the user’s digital signature. As a result, every time you encrypt a message using the public key, your private key ensures that the message is coming from you.
Public Keys – Your private key is used to derive the public key using complex mathematical algorithms. A public key is the key that senders can share with the receiver.
Private and Public Keys always work in pairs for encrypting and decrypting messages respectively.
The only difference is that public keys are more like your email address that you can share to the world to receive emails. Whereas, private keys are the password you need to authenticate your email ID, so that you can access your inbox.
However, unlike your email ID and password, setting up a private key and public key requires a few extra steps. Learn more about private and public keys.
Types of Cryptocurrency Wallets
Now that there is some understanding of what private and public keys are, let’s check out the options we have for storing them.
The TWO main categories of wallets are :
Hot – Hot wallets require connectivity to the internet to function. There are 3 types of wallets that fall under this category: Web Wallet, Desktop Wallet, and Mobile Wallet.
- Pros: generally considered easy to use
- Cons: susceptible to network hacks, phishing scams
Cold – Cold wallets exist as a separate physical entity that is disconnected from the internet. 2 types of wallets fall in this category : Hardware Wallets and Paper Wallets
- Pros: generally considered safer
- Cons: tedious in terms of set up and access to coins
Let’s delve deeper.
Web Wallet
This is the first type of wallet everyone comes across when beginning to purchase and store cryptocurrencies. These wallets can be easily accessed via web browser. A number of crypto exchanges and software provide this feature online and make the interface incredibly easy for users. In many cases, web wallets offer to secure the private keys on behalf of the user. The entire thing revolves around placing a significant amount of trust. Some of the most popular web wallets (also known as software wallets) are Coinbase, Binance, Gemini, etc.
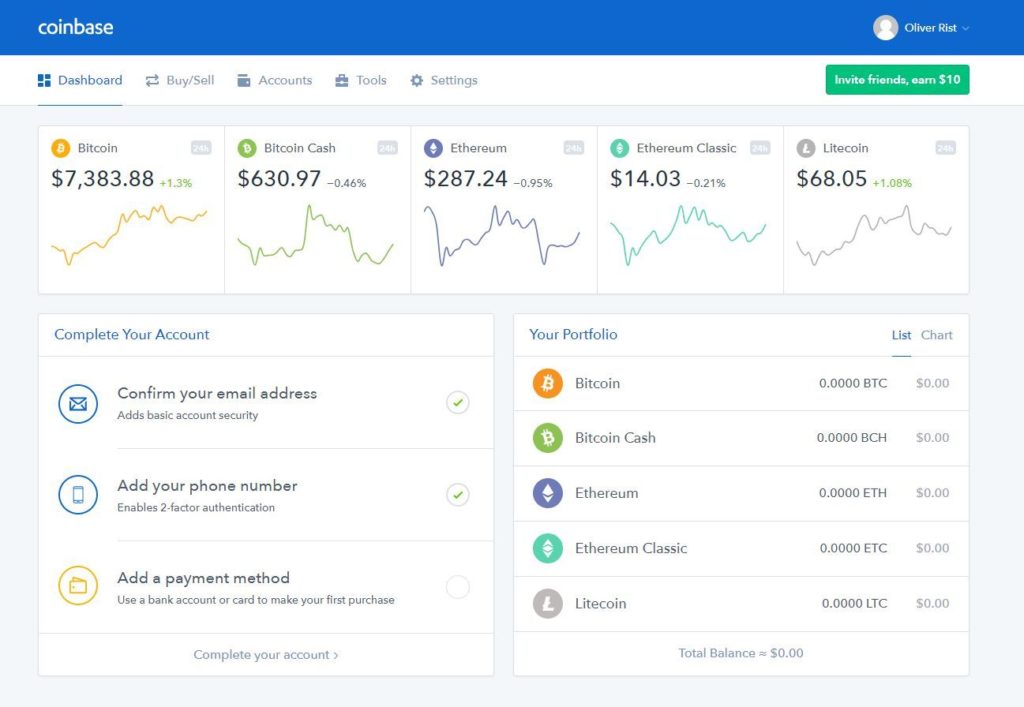
Pros :
- Fast Transactions
- Transfer between cryptocurrencies are easier
- Good for those just beginning to get a taste of crypto storage (and for one’s who invest a small amount)
Cons :
- Prone to malwares, phishing scams, breach of security measures, and a host of other security related issues.
- Your wallet is technically stored with a third party
- High requirement for trust in the third party
Mobile Wallet
It’s the same as a web wallet, except it can be downloaded to and managed via your smartphone.
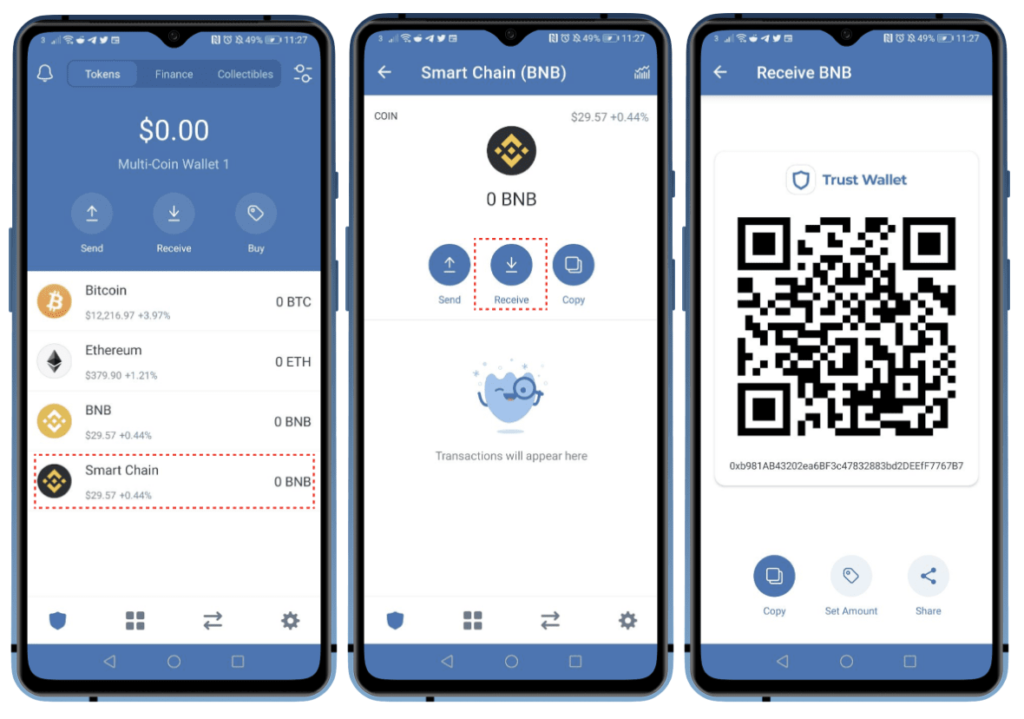
- Pros: Same as Web Wallet with the added benefits of portability and QR code scanning
- Cons: Same as Web Wallet with the additional problem of losing access if your phone gets stolen or lost.
Desktop Wallets
Within the Hot Wallet (hot storage) category, desktop wallets are safer than the other two, mainly because it shifts your wallet away from the clutches of a third party. However, the security of your keys depends on how well protected your computer is. Some of the popular ones are Electrum, Exodus, Guarda, etc.
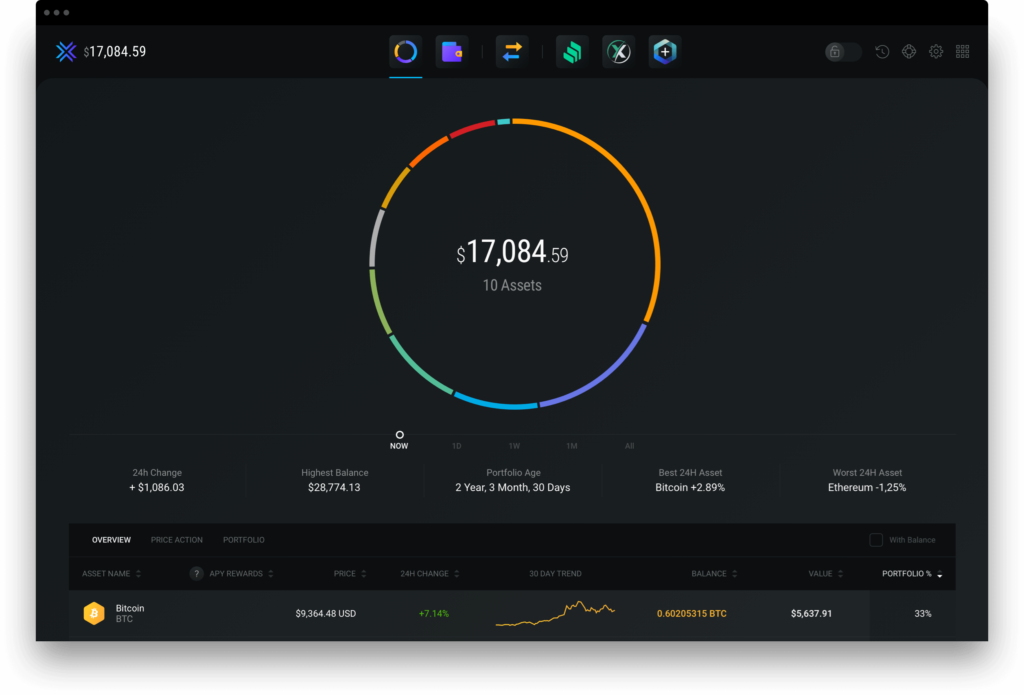
Pros
- Keys stored away from third parties
Cons
- Considering you are connected to the internet, all of the malware, virus attacks coming from downloading malicious files apply here too.
- If your computer breaks down, sending it to repair can be like serving your keys on a silver platter.
- Complete loss of access if your system has been stolen
- No Backup = No chance of data retrieval
Clearly, hot wallets seem quite unreliable in the sense that security is as thin as the skin of an apple. The only advantage is that because they are easier to use, it’s a great way for someone with a small investment to understand crypto wallets.
Hardware Wallets
If you have heard about investors endorsing Ledger Nano S, Ledger Nano X, Trezor One, you must be wondering;
“What does a USB-stick-looking-thing have to do with security?”

Hardware wallets such as the ones mentioned above are basically a physical device that resembles a flash drive. Hardware wallets are used to store your private keys.
Pros:
- Always stay disconnected from the Internet
- Safe enough to use on computers with viruses and malware attacks.
- Ideal for those holding large amounts of cryptocurrencies
- Ideal for those wanting to hold their assets long term
- You never expose your private keys to your device during transactions
- Requires a pin code to unlock device on the computer
Cons:
- Tad difficult for beginners to understand
- If stolen or broken, you lose private keys forever.
- Susceptible to a lot of counterfeit products, hence it’s crucial to buy the device from a trusted manufacturer.
- Recovery phrase can be susceptible to theft if not protected properly, similar to a paper wallet
Paper Wallet
Literally a printed piece of paper containing a QR code to unlock your keys. Prior to hardware wallets, paper wallets were the gold standard for hacker-proof storage.

Pros: Similar to Hardware Wallets except for the requirement of a pin code
Cons:
- Ink fading during printing process could make scanning the QR code difficult
- If someone can access the location of your paper, they can physically steal it
- Malwares in printers connected to a larger network
Basically, paper wallets are somewhat obsolete due to issues stemming from the printing process itself.
If you are looking to invest in cryptocurrency long term, ideally the best option is to utilize a hardware wallet. Some experts recommend a combination of software and hardware wallets. Software for smaller funds that require immediate movement. Hardware wallets for storing large amounts of your assets.
When it comes to cryptocurrency wallets, it is up to you to strike the right balance between convenience and rock-hard security.


Leave a Reply